EXPLOITATION
One of the cornerstones of Netsparker’s design is its ability to automatically exploit suspected vulnerabilities in a safe and read only way, proving them beyond doubt and reporting no false positives. But this unique feature becomes all-the-more powerful when it is used to probe even deeper, allowing you to visualize the impact in real time and even to discover related vulnerabilities that would otherwise be undetectable.
AUTOMATED EXPLOITATION OF VULNERABILITIES
Netsparker is the only web application security scanner with an integrated exploitation engine. By exploiting detected vulnerabilities in a safe and non-destructive manner, Netsparker is often able to yield additional detail about security vulnerabilities that would be completely undetected by conventional security scanning techniques.
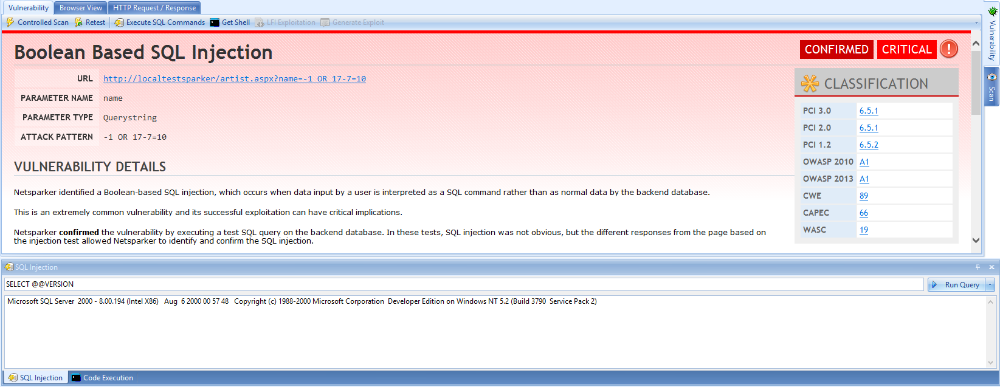
For example, when Netsparker detects an SQL Injection vulnerability, it is able to query the database engine to obtain data that may reveal additional vulnerabilities in its configuration or patch status.
INTEGRATED EXPLOITATION
For certain types of vulnerabilities, Netsparker offers an integrated exploitation module that allows users to interactively exploit the vulnerability and see the real impact of an attack. Netsparker currently supports:
- Exploitation of SQL Injection Vulnerabilities
- Exploitation of LFI (Local File Inclusion) Vulnerabilities
- Downloading source code of all crawled pages via LFI (Local File Inclusion)
- Downloading known OS files via LFI (Local File Inclusion)
- Exploitation of Remote Code Evaluation
- Obtaining a reverse shell from exploiting SQL Injection, Remote File Inclusion and other vulnerabilities
- Cross-site Scripting PoC generation
-lw-scaled.png.png)